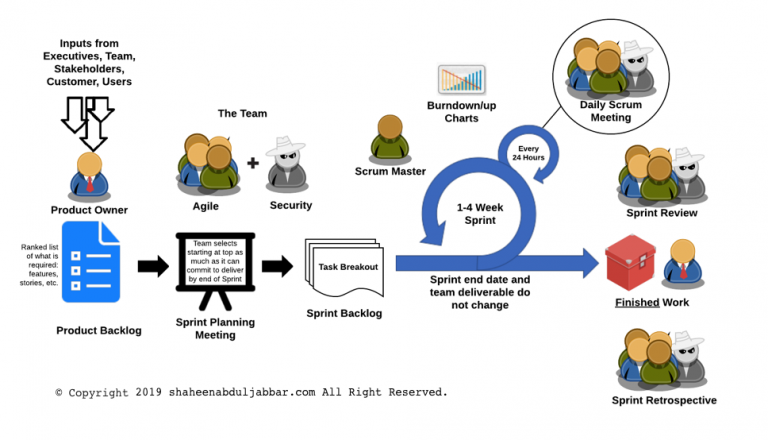
Many large organizations are moving towards the Agile software development lifecycle (SDLC) methodology. Agile methodology is a combination of iterative and incremental process models with a focus on process adaptability and customer satisfaction by rapid delivery of working software product. The general characteristics of any Agile methodology are: Prioritizing feedback. Agile teams rely heavily on the… Continue reading Security in Agile Methodology
Career in Cybersecurity
There was a time when you say you work in cybersecurity people would misunderstand you to be a security guard for some unheard company. Not anymore! Today cybersecurity is in the mainstream. If you are in the business of protecting internet-connected systems, including hardware, software, and data, from adversaries, then you are already a cybersecurity… Continue reading Career in Cybersecurity
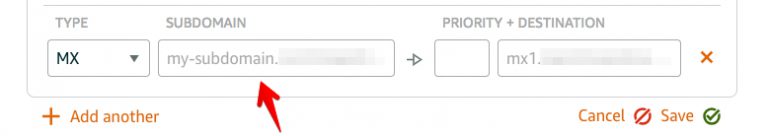
MX Records on Amazon Lightsail
Are you considering moving your Name Server to Amazon Lightsail? You may end up looking for what that “subdomain” means for the MX records. As someone who volunteers for non-profits, I have the opportunity to try out Gmail from G-Suite. As of today (August 25, 2018), Google is yet to provide documentation for Amazon Lightsail… Continue reading MX Records on Amazon Lightsail
Best of Breed or Best Suite of Products
Should organizations implement layered defenses from different vendors? Should we rely upon a single vendor for an organization’s overall security? According to a Gartner research paper, “Two firewall platforms are not better than one. We believe there is a higher risk associated with configuring and managing firewalls from multiple vendors than from a single vendor.… Continue reading Best of Breed or Best Suite of Products
Hardware or Host Based Firewalls
Do organizations need hardware firewalls when the network already has host-based software firewalls? Wouldn’t it add cost and complexity to networks? Wouldnt system protected by host-based software firewalls just as secure as having a hardware firewall if they are implemented appropriately? “Firewalls actually come in two distinct flavors: software applications that run in the background… Continue reading Hardware or Host Based Firewalls
Acknowledging Non-Applicable Threats
Is it important to account for or acknowledge risks that may not apply to an organization or system? What if you identified a risk that you would typically consider for but would not use due because of the context. Say, for example, your organization is not in a floodplain however it is usual to consider… Continue reading Acknowledging Non-Applicable Threats
Cloud Computing and Data Security
We cannot attribute the beginning of cloud computing to a particular person or time. It evolved with the evolution of Internet and enterprise computing. We may be able to trace its roots all the way back when Dr. Larry Roberts developed the ARPANET in 1969. (Whitman & Mattord, 2016) While the evolution of ARPANET, to Ethernet… Continue reading Cloud Computing and Data Security
Reporting Illegal or Unethical Behavior
What should employees do if they discover unethical or illegal behavior? Should they raise concerns without fears of retaliation? Employees are doing a favor for the company and its stakeholder by raising concerns about unethical or illegal behaviors. One day or the other, the act will come to light, and it will cost the company… Continue reading Reporting Illegal or Unethical Behavior
Roles of Management and Technology in InfoSec
Information security is both a management issue and a technology issue. The management of an institution could be the owner or custodian of the data that their information security program is trying to protect. They need to ensure that the systems they employ execute all the functions on the data as they are supposed to… Continue reading Roles of Management and Technology in InfoSec
Who doesn’t need to be concerned about InfoSec?
Would there be any person or group within an organization that does not need to be concerned with information security? The only person who need not worry about information security is the one who has no value bearing data. Unfortunately, in this day and age, every single person who is connected to modern world has… Continue reading Who doesn’t need to be concerned about InfoSec?